Getting breached by two separate and likely unconnected cyber attack groups is a nightmare scenario for any organization, but can result in an unexpected silver lining: the noisier intrusion can draw attention to a far stealthier threat that might otherwise linger undetected for months.
A double whammy
In a recently published report, threat researchers at Positive Technologies have detailed the findings of their investigation into two incidents at Russian companies, which they have tied to:
QuietCrabs, a threat actor believed to be of Asian origin and concentrating on cyber espionage, and
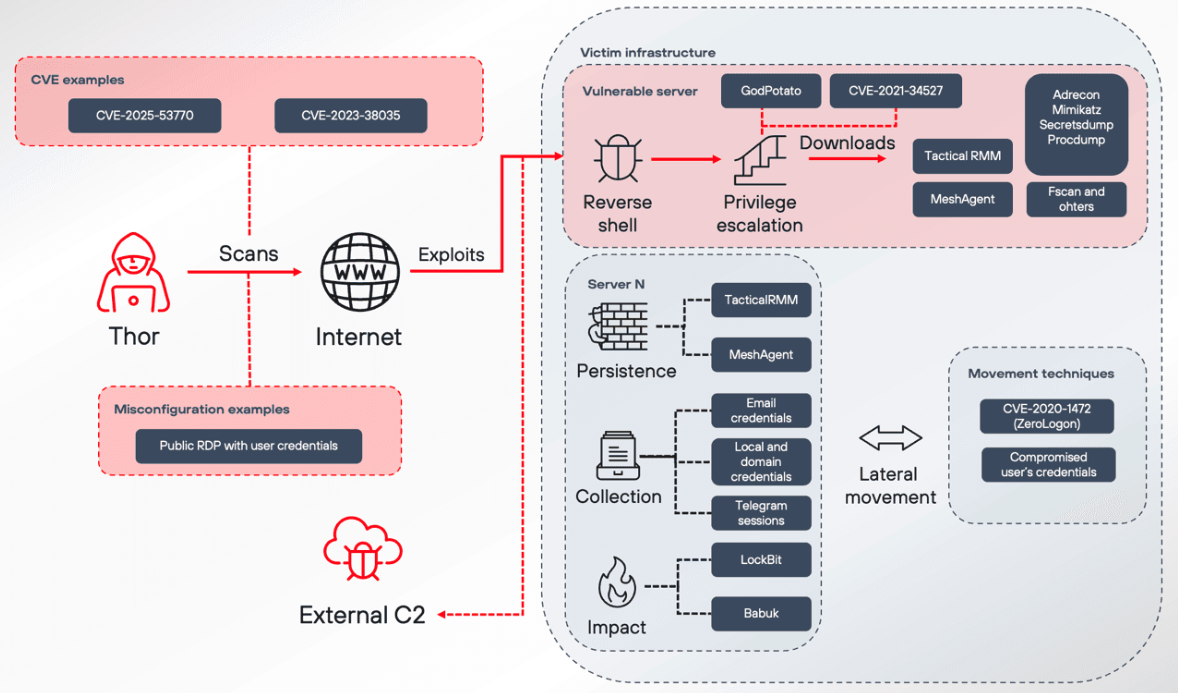
Thor, a threat group that has been targetting Russian companies with LockBit and Babuk ransomware.
Both groups exploited publicly known vulnerabilities in Microsoft Sharepoint Server (CVE-2025-53770) and Ivanti’s solutions (CVE-2024-21887, CVE-2025-4427, CVE-2025-4428, CVE-2023-38035) to achieve initial access.
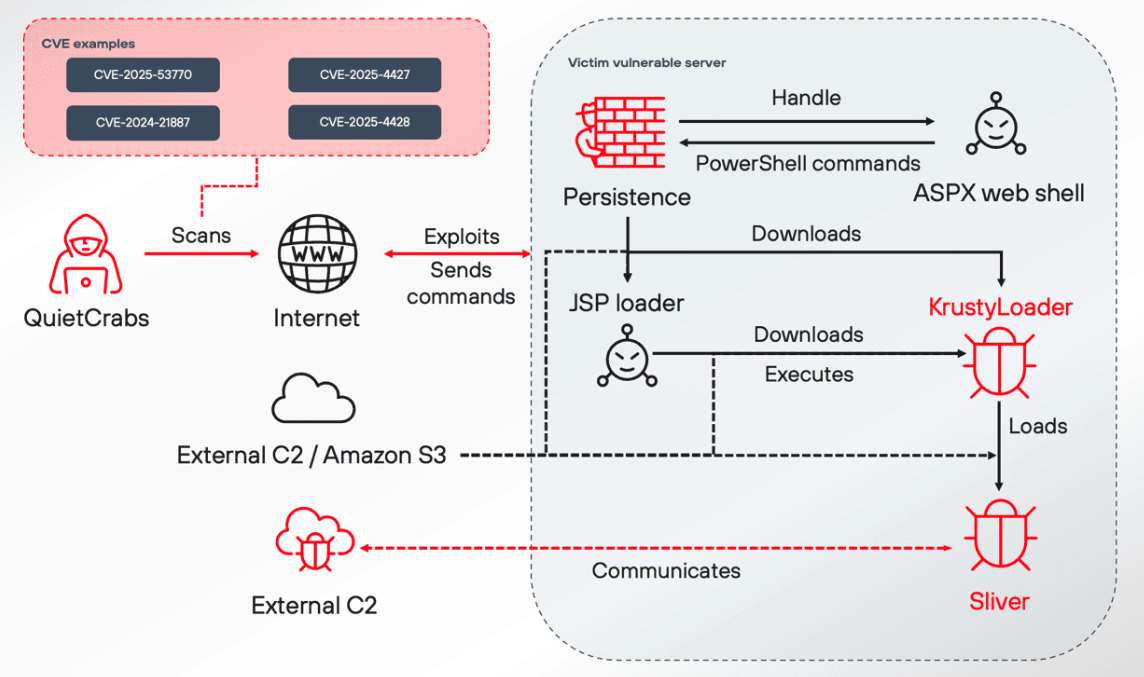
QuietCrabs attack flow (Source: Positive Technologies)
QuietCrabs leveraged an ASPX web shell, the KrustyLoader (loader) malware, and the Sliver command & control implant. Thor, on the other hand, uses well-known and widely used tools:
The ADRecon utility (for Active Directory domain reconnaissance)
The GodPotato tool (for privilege escalation)
Secretsdump and Mimikatz (for data extraction)
Tactical RMM and MeshAgent (for persistence), and
Rclone (for data exfiltration.)
In this case, though, Thor’s presence was detected early enough to foil the deployment of ransomware.
“QuietCrabs and the presumed Thor group operated in almost the same time period. The gap between their malicious activities was only a few days,” the threat researchers noted (though didn’t mention when the attacks actually happened).
“It is also important that the investigation began at the point where Thor activity was first registered. In other words, QuietCrabs could have remained inside the infrastructure for much longer if not for Thor. According to Mandiant’s investigations, QuietCrabs’ average dwell time in victim infrastructure is 393 days.”
The researchers are almost entirely certain that one of the intrusions was by QuietCrabs, as the KrustyLoader is unique malware that’s associated with that group. “Some vendors describe KrustyLoader exclusively as Linux malware. In our case, however, all incident artifacts were Windows samples,” they shared.
The other, more noisy activity has been attributed to Thor based on indicators of compromise that matched a previous attack report by another Russian cybersecurity company.
Thor attack flow (Source: Positive Technologies)
ToolShell: A magnet for various threat actors
In July 2025, after reports of CVE-2025-53770 (aka ToolShell) having been exploited as a zero-day by Chinese threat actors Linen Typhoon and Violet Typhoon against organizations worldwide, Microsoft confirmed that a financially motivated China-based threat actor (Storm 2603) has also been using the vulnerability to achieve access and deploy Warlock ransomware.
“We cannot confidently state that QuietCrabs is collaborating with Thor. In this case, the overlap is most likely coincidental, as both QuietCrabs and Thor conduct broad scans of organizations for subsequent compromise,” the PT researchers opined.
While they say that QuietCrabs has been targeting organizations in the US, UK, Germany, South Korea, Russia, Taiwan, the Philippines, Iran, the Czech Republic, and a number of other countries, Thor’s victims appear to be mostly Russian orgs.
“We were able to identify around 110 Russian companies as potential victims. The affected organizations varied greatly both in economic sector and in the potential profit they offered the attackers,” they concluded.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!