The internet can be a pretty scary place, and while we use privacy-focused browsers, know what phishing attempts look like, and use password managers to keep our secrets safe, another piece of information gets siphoned off every time you navigate to a new webpage. At least, if you’re still using the DNS servers that your ISP or cellular provider set up when you first got service, because those plaintext queries get stored and sold to advertisers and anyone else who might want to get their hands on the information they hold.
If you care about your online privacy, it’s time to stop using your ISP’s DNS servers. You don’t have to self-host a DNS server if you don’t want to, but take a little time to research an external DNS provider that uses encrypted methods, and switch to that on all your devices. Every little piece of data you can claw back from your ISP and other data hogs is worth the effort.
The problem with your ISP’s DNS
Okay, problems, plural, because they’re not your friend
There are many reasons you’d not want your ISP resolving your DNS queries, but most of them boil down to one thing — privacy. ISPs are lousy at this, whether it’s not enabling DNSSEC to ensure DNS responses are authentic and untampered with, or bundling your browsing habits into nice packages to sell to advertisers as supposedly anonymous data. In a world where all data is for sale, sending out unencrypted DNS records is another way for you and your habits to be tracked.
The other thing that your ISP does is network-level DNS blocks of any resources or websites that they deem unsafe, potentially cutting off access to chunks of the open internet. That could be a good thing, if they’re blocking known malware sources, but it doesn’t take much of an imagination to see it potentially used for blocking adult content, tools for video game preservation, or anything that the ISP decides to block (or gets a legal notice from the government to do so).
By moving to another DNS provider, you sidestep any ISP-level blocks. It doesn’t guaranteed your new DNS provider doesn’t have its own blocks, but these are generally more forthcoming about what and why they’re blocking certain content, and it’s mostly for the user’s benefit and safety.
You don’t have to self-host DNS
Many of the commercial alternatives are safe and secure
There are plenty of private DNS providers worldwide to get encrypted DNS set up with the minimum of fuss. You don’t have to self-host anything to use these options; instead you change the DNS server on every device you want to use it on, from your router to smartphones and more. That gives your devices better security, circumvents any ISP-level blocks to DNS resolution, and helps you stay more private when online.
While encrypted DNS will keep your ISP from seeing your DNS queries, it’s not going to keep your browsing private. You’ll need a VPN or other securely encrypted method of accessing the internet for that.
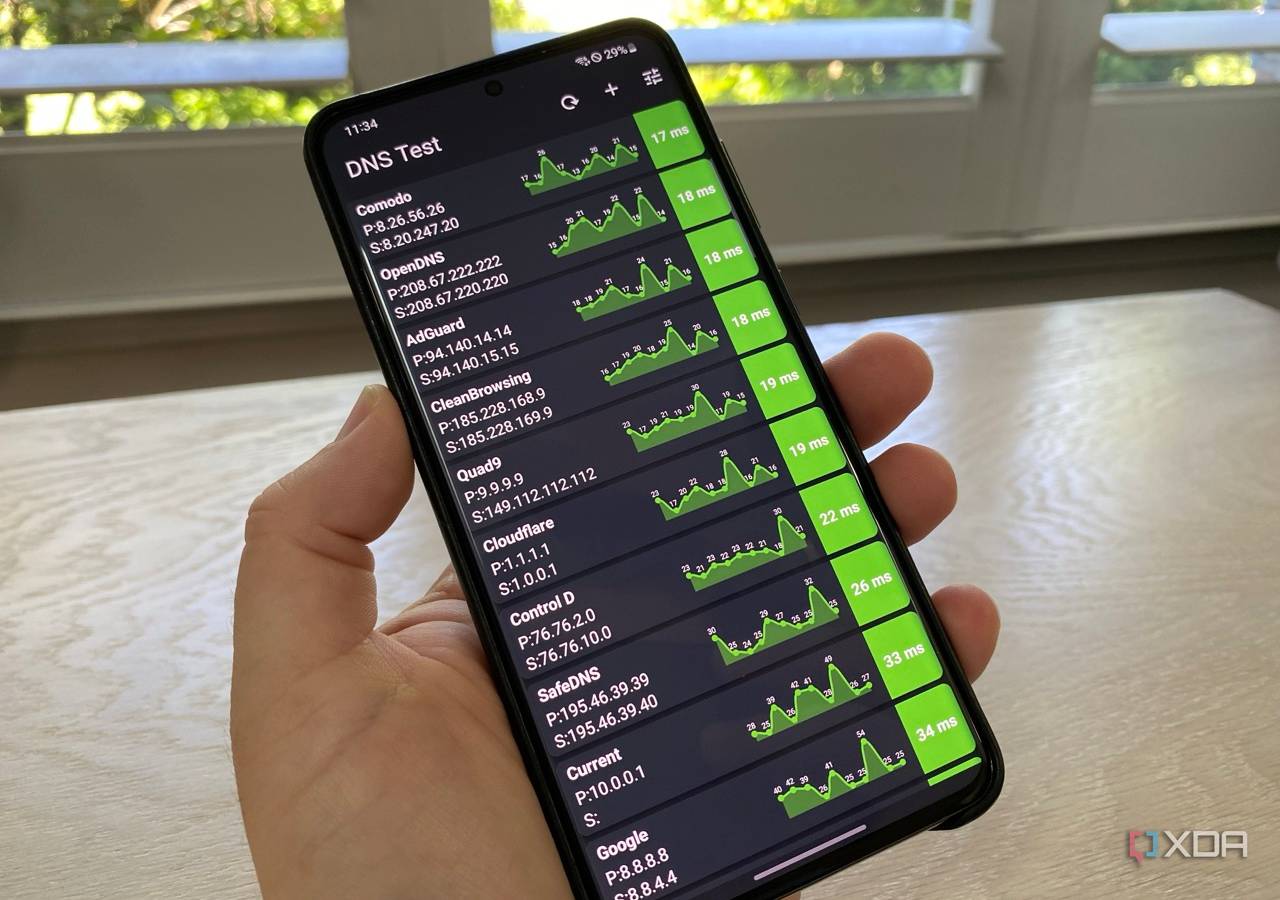
You’ll want to make sure the DNS provider you choose supports DNSSEC, QNAME Minimization, and also either disable or anonymize EDNS Client Subnet (ECS) if it’s available. Also, you don’t want it to log personal data to disk, and it should support anycast or geo-steering.
In no particular order, each of these DNS providers will be more secure and private than your ISP’s:
Cloudflare (1.1.1.1): Runs a large chunk of the internet, known for not blocking sites unless known as a threat
Quad9 (9.9.9.9): Encrypted DNS, also known for not blocking sites without them serving malware or other threats
Control D (76.76.2.2): No logging, various encryption methods, and works on Apple devices
AdGuard Public DNS: Anonymized, uses some filtering, has Apple profiles.
These should all also support various encrypted options, including DNS-over-HTTPS, DNS-over-TLS, or DNS-over-Quic. And with how often DNS goes wrong, it’s always a good idea to use a trusted DNS solution for the best and most secure option.
But self-hosting gives you more control
You get ad-blocking, locally resolved domains, and more
Self-hosting a DNS server is deceptively simple to do these days, whether you choose from any of the options, including Unbound, AdGuard Home, PowerDNS, or my personal favorite, Technitium. You’ll still want to have some queries sent to an external DNS server in an encrypted manner for fallback, but having your own local DNS server making its own encrypted requests will increase the security and privacy of your home network and the devices using that DNS server.
You get all the bonuses of using an existing DNS provider, like ad blocking at the source, plus you can set up zones, split horizon DNS so that different devices on your network get different DNS results, and local domain rebinds, which are very handy for home lab use. Add in dnscrypt-proxy as a local frontend (if needed), and your DNS requests are unreadable by your ISP. Finally, block port 53 to force every device to use your new local DNS server via encrypted egress, and you’re in (relative) control over your DNS queries.
Whatever you choose, it’s time to stop using your ISP’s DNS servers
Using the DNS servers your ISP defaults to might be easy, but it’s not good for your online privacy. Plus, your DNS data is likely being sold for advertising use, along with any other data that the ISP can sniff. Using an encrypted DNS provider means your ISP is cut out of the loop, so while it doesn’t make your browsing private, it does reduce the exposure of your online usage. And it’s not just your browsing habits, because your location can be triangulated with DNS queries, and that’s possibly more worrisome.