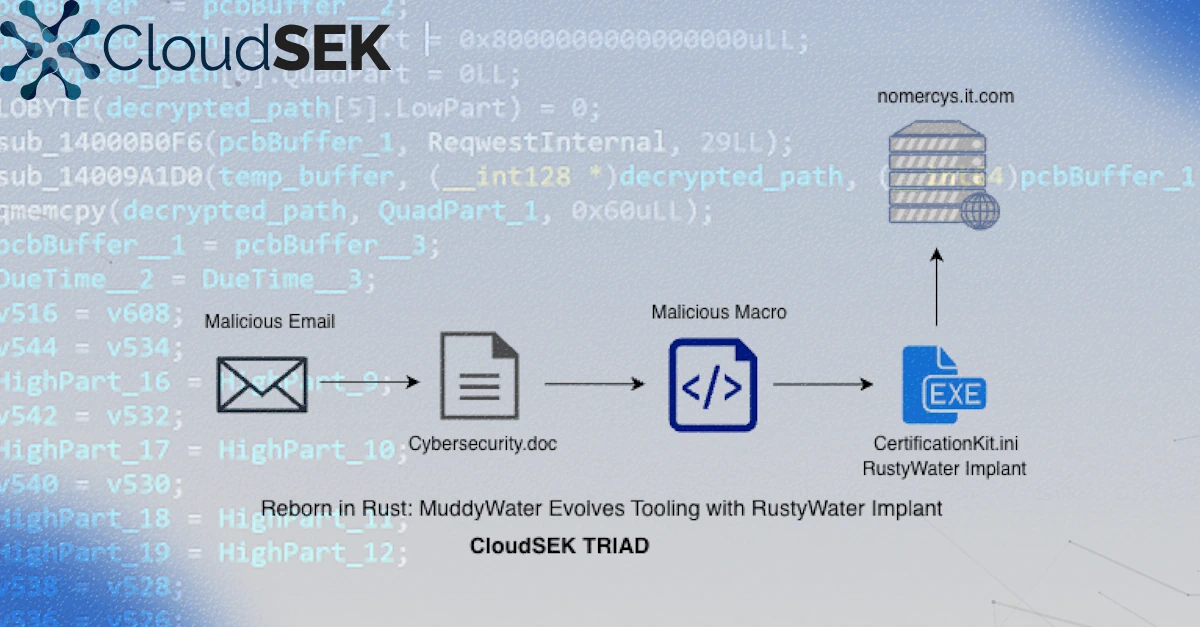
New research from CloudSEK’s TRIAD recently identified a spearphishing campaign attributed to the Muddy Water APT group targeting multiple sectors across the Middle East, including diplomatic, maritime, financial, and telecom entities. The campaign uses icon spoofing and malicious Word documents to deliver Rust-based implants capable of asynchronous C2, anti-analysis, registry persistence, and modular post-compromise capability expansion.
“Historically, Muddy Water has relied on PowerShell and VBS loaders for initial access and post-compromise operations. The introduction of Rust-based implants represents a notable tooling evolution toward more structured, modular, and low noise RAT capabilities,” researchers detailed in a Thursday post. “Although this Rust-based implant has appeared in limited reporting under names like Archer RAT / RUSTRIC, it remains far less documented than Muddy Water’s legacy PowerShell/VBS tooling. To avoid name collisions and for sanity, we refer to this variant as RustyWater throughout this report.”
The post explained that the email titled ‘Cybersecurity Guidelines’ was sent from the email domain ‘info@tmcell,’ which looks to be an official contact email for TMCell (Altyn Asyr CJSC), the primary mobile operator in Turkmenistan. There is also a document attached called ‘Cybersecurity[dot]doc, which serves as the primary payload for the next stage.
“We can run oleid to identify if any macros are present in the document and dump them further using tools like oledump,” the post added. “WriteHexToFile reads a hex-encoded byte stream embedded in UserForm1.TextBox1.Text removes all formatting characters, validates the data length, and decodes it into raw binary. It then writes the reconstructed payload to disk as CertificationKit.ini in C:\ProgramData\.”
The next love_me_function is primarily an obfuscated execution wrapper. It begins by dynamically reconstructing the string WScript.Shell uses hard-coded ASCII values and the Chr() function.
Once reconstructed, the function validates the string and uses CreateObject to instantiate a WScript[dot]Shell COM object to build a second obfuscated string that resolves to cmd[dot]exe and executes CertificationKit.ini, the file written earlier by ‘WriteHexToFile’ function.
RustyWater begins execution by establishing anti-debugging and anti-tampering mechanisms. It registers a Vectored Exception Handler (VEH) to catch debugging attempts and systematically gathers victim machine information, including username, computer name, and domain membership. All strings in the malware are encrypted using position-independent XOR encryption.
CloudSEK found that RustyWater attempts to detect a wide range of antivirus and EDR tools by scanning for agent files, service names, and installation paths of more than 25 AV products.
“The malware sets up persistence by writing itself to a Windows startup registry key. It first decrypts the key path and then opens the Run registry location under the current user,” according to the post. “If that fails, it crashes with a Rust error message. Next, it decrypts another short string that becomes the name of the startup entry. The value points to a file at C:\ProgramData\CertificationKit.ini, which is our payload.”
It added that the malware establishes HTTP-based command and control using the Rust reqwest library. It configures timeouts, connection pooling, headers, and implements retry logic for reliable C2. “Before transmission, the binary encodes collected data using base64 and encrypts it. The payload is structured as JSON and includes system information, file listings, and metadata. The entire encryption is done with 3 layers of obfuscation(JSON -> Base64 -> XOR). To avoid detection, the binary implements randomized sleep intervals between C2 callbacks. It uses waitable timers and random number generation to create jitter, making traffic analysis difficult.”
Based on the technical artifacts, targeting patterns, and tactical similarities observed in this campaign, we assess with high confidence that this activity can be attributed to Muddy Water APT (also tracked as Earth Vetala, MERCURY, Static Kitten, Mango Sandstorm).
Several technical indicators support this attribution. The VBA macro code extracted from Cybersecurity.doc shows strong similarities to previously documented MuddyWater campaigns, including the reuse of the WriteHexToFile and love_me_ functions. These patterns feature the distinctive embedding of hex-encoded payloads within UserForm controls, a technique consistently observed in earlier MuddyWater operations.
The campaign analysed in this report shares a significant overlap with another report. Similar TTPs can be observed in that chain, too, where the initial email was impersonating the L.M. Group, a legitimate Israeli HR company.
The impact includes a high risk of long-term silent persistence, as registry-based autostart mechanisms and delayed beaconing allow the Rust implant to survive reboots while leaving minimal forensic artifacts on disk. The threat actor can also dynamically expand post-compromise capabilities, with modular implants enabling new functions such as data collection, command-and-control tasking, or credential theft without the need to deploy additional binaries or reestablish access.
Static network countermeasures are less effective in this scenario because tiered command-and-control failover, request jitter, and protocol switching reduce the detection value of domain or IP blocking and signature-based filtering. Incident response teams face limited visibility, as in-memory execution and asynchronous task handling complicate timeline reconstruction, memory analysis, and confident attribution. The approach further increases targeting and intelligence collection risk, since on-demand module deployment allows surveillance to be tailored to the victim’s role, including diplomatic, maritime, or telecommunications environments, expanding the scope of potential data exposure.
CloudSEK recommended monitoring registry-based persistence mechanisms and flagging user-context processes that modify autostart locations. Detection efforts should focus on layered command-and-control behavior rather than single indicators, with alerts triggered by retry-heavy outbound HTTP traffic, randomized callback intervals, fallback domains, and multi-step data transformation patterns that move from JSON to Base64 to XOR.
Security teams should instrument memory allocation and thread manipulation events, hunting for activity that combines VirtualAllocEx, WriteProcessMemory, and thread context modification within otherwise benign Windows processes such as explorer.exe. It is also important to correlate signer trust with execution locality by flagging signed binaries executed from writable paths like Downloads, Temp, or ProgramData when they are followed by non-signed module loads or remote thread creation. Late-stage remote access trojan capability activation should be treated as malicious, with monitoring in place for shifts from passive beaconing to active collection behaviors such as file enumeration, keylogging, credential harvesting, or task execution.

Anna Ribeiro
Industrial Cyber News Editor. Anna Ribeiro is a freelance journalist with over 14 years of experience in the areas of security, data storage, virtualization and IoT.