Researchers have found that many low-cost Android devices come with pre-installed apps that have high-level access to the system. Unlike apps from the Google Play Store, many of these are not subject to thorough checks and can serve as vectors for malware or privacy-invasive features.
Researchers studying the African mobile device market focused on three brands selling Android devices under $100, all running Android Go Edition. To investigate, the team developed PiPLAnD, an automated framework for extracting and analyzing Android package kit (APK) files from physical devices.
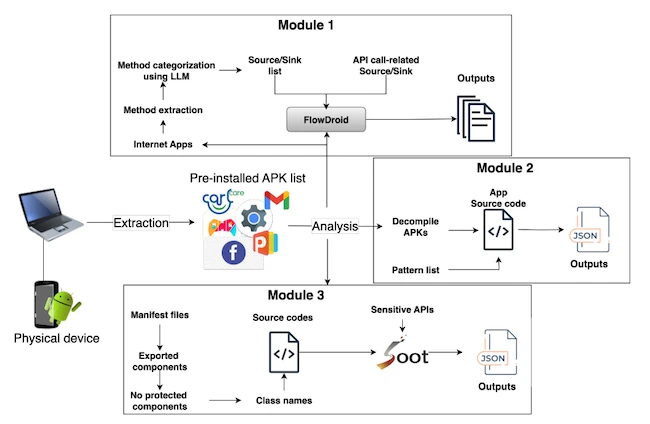
Overview of PiPLAnD ’s workflow
Android Go Edition
Android Go Edition is a lighter version of Android made for entry-level devices with limited memory (2 GB or less) and storage. It comes with simplified versions of Google apps, but users can still install apps from the Play Store. Updates may arrive less frequently than on standard Android.
Apps leaking sensitive data
One of the main findings of the study was the exposure of sensitive personal data. The types of data exposed include Mobile Country Code (MCC), user location (latitude and longitude), device details, International Mobile Subscriber Identity (IMSI), and International Mobile Equipment Identity (IMEI).
These leaks happen in several ways, through SharedPreferences, device logs, Intents, and even over the network. Overall, about 9% of the pre-installed apps analyzed, 145 apps in total, were leaking sensitive information.
Suspicious behaviors on pre-installed apps
Some pre-installed apps can install other apps without the user’s knowledge, while others can access or steal sensitive data.
To identify these threats, analysis focused on detecting patterns. For example, apps that declare the INSTALL_PACKAGES permission can install apps silently using android.content.pm.PackageManager.installPackage() or Runtime.exec(‘pm install’). In total, 33 apps on the devices studied exhibited this silent installation behavior.
Many pre-installed apps can access SMS messages through the content://sms provider. Some can delete messages or use the SEND_SMS and RECEIVE_SMS permissions with the broadcast action Telephony.SMS_RECEIVED, allowing them to read and send messages. Around 79 apps had this level of SMS access.
At least 10 apps can access logcat content. With the READ_LOGS permission, these apps can read logs from other apps as well. Additionally, 226 apps were found to be capable of executing potentially dangerous commands.
Security misconfigurations on the manifest files
Android apps can export components like activities, services, receivers, and providers. This can be done by setting android:exported=”true” or by declaring an intent-filter in the manifest file. When a component is exported, other apps can launch it.
Access to exported components is usually controlled with permissions. If a component requires permission, any app that wants to use it must declare that permission. If a component is exported without enforcing permissions, any app can launch it or access the data it contains.
Analysis shows that several pre-installed apps have exported sensitive components. About 16% of the pre-installed apps analyzed, representing 249 app versions, had exported sensitive components on low-cost devices without any protection. This potentially puts users at risk because their data could be accessed by third parties.
Broader implications
This study does not suggest that all budget Android devices are unsafe, nor does it examine every market. Its focus was on a sample of devices that represent typical low-cost Android options. Still, the research provides evidence that preinstalled apps deserve more scrutiny.
For consumers, the study shows that the risk is not only about which apps they choose to install. The software that comes with the phone can already contain privacy and security issues. This is especially important for people who use these devices for personal or professional purposes where sensitive information might be stored.

