The increasing demand for secure communication drives research into methods that protect information even when parts of a network are compromised. Wai Ming Chan from Arizona State University, Remi Chou from The University of Texas at Arlington, and Taejoon Kim, also from Arizona State University, present a novel approach to this challenge, introducing the first two-dimensional secret sharing scheme based on simple XOR operations for layered multipath communication networks. This construction guarantees successful message recovery and complete privacy, even if an attacker disrupts any single communication path at each layer, and crucially, achieves this with provable, information-theoretic security. Unlike conventional encryption methods susceptible to evolving computational power, this scheme offers a robust and verifiable level of protection, making it particularly valuable for resource-limited applications such as secure military communications where reliance on unproven assumptions is unacceptable.
The scheme ensures both availability and perfect privacy, even when network components are compromised. Key achievements include a new 3×3 secret sharing scheme that distributes a secret across multiple base stations and routes, leveraging XOR operations for simplicity and efficiency. The system is mathematically proven to guarantee availability, allowing secret reconstruction even with the loss of an entire base station and route, and perfect privacy, ensuring an adversary intercepting a row and column of the matrix gains no information about the original secret.
Its lightweight design, based on XOR operations, makes it suitable for devices with limited processing power, while a robust integrity check verifies the shared secret’s authenticity. Rigorous mathematical proofs, based on information-theoretic principles, demonstrate the scheme’s security properties. The method involves splitting the secret into multiple shares using XOR operations with random sequences, distributing these shares across base stations and routes, and reconstructing the original secret using XOR operations even if one base station and one route fail. Privacy is maintained because the random sequences used in the XOR operations prevent attackers intercepting shares from gaining any information about the secret. This scheme is specifically designed for military communications where reliability, security, and resource constraints are critical, offering a practical and secure solution for protecting sensitive information in challenging communication environments.
Two-Dimensional Secret Sharing for Layered Networks
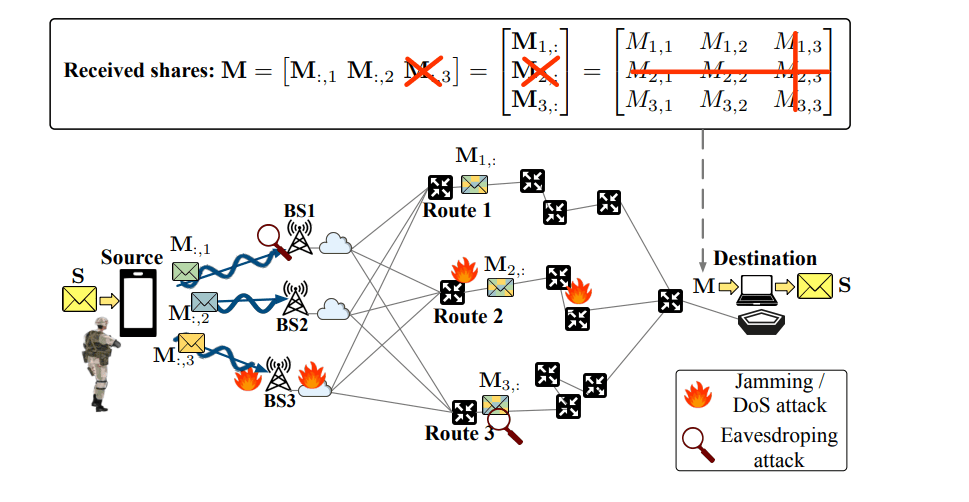
The research team engineered a novel two-dimensional XOR-based secret sharing scheme for layered multipath communication networks, achieving both perfect privacy and robust availability. This work pioneers a method where a secret message is divided into two equal segments and encoded using XOR operations with independent binary sequences, generating intermediate share vectors. These vectors are routed to three base stations, with each forwarding components along three distinct routes, creating a 3×3 share matrix. This configuration, while scalable to general network topologies, initially focused on a 3×3 grid to demonstrate the fundamental principles of two-dimensional secret sharing.
The 3×3 matrix represents a network where each cell embodies a complete communication path, abstracting away internal network details to ensure robustness against dynamic topology changes. The team rigorously analyzed the scheme’s performance under a computationally unbounded adversarial model, considering both passive observation and active disruption. Employing information-theoretic concepts, the researchers demonstrated that even with the loss of one base station and one route, the original secret message can be fully recovered. Furthermore, they mathematically proved perfect privacy, showing an eavesdropper observing shares through one base station and one route gains zero information about the secret message. This achievement relies on bitwise XOR operations, minimizing computational overhead and making the scheme suitable for resource-constrained environments.
Perfectly Private Secret Sharing via Share Matrices
Scientists have developed a novel secret sharing scheme for communication networks with multiple pathways, achieving both data availability and perfect privacy. This work introduces the first two-dimensional scheme of its kind, utilizing only bitwise XOR operations for efficient computation and minimal overhead. The system divides a secret message into two equal segments and encodes it into a 3×3 share matrix, distributing portions across multiple communication routes and base stations. The encoding process leverages random binary sequences, generated solely at the encoder, to create intermediate shares, strategically arranged within the matrix to ensure the original message can be fully recovered even if an adversary disrupts a single base station or communication route.
Mathematical proofs demonstrate the scheme guarantees recovery of the secret from any combination of surviving shares, even with a single point of failure. Crucially, the research establishes perfect privacy, meaning an eavesdropper intercepting shares transmitted through one base station and along one route gains absolutely no information about the original secret. Measurements confirm the mutual information between the intercepted shares and the secret is zero, demonstrating complete information-theoretic security. This is achieved through careful arrangement of the shares and the exclusive use of XOR operations, eliminating vulnerabilities associated with traditional encryption methods. The system’s design minimizes computational complexity, making it particularly well-suited for resource-constrained environments, such as military applications, where security assumptions may not hold. By extending a previously developed one-dimensional scheme, the team has created a robust and efficient method for secure communication in complex network topologies, delivering a provably secure system independent of computational power, even against adversaries with quantum computing capabilities.
XOR Scheme Secures Layered Network Communication
This research presents the first two-dimensional secret sharing scheme based exclusively on XOR operations, designed for layered multipath communication networks. The scheme successfully addresses the challenge of maintaining both message availability and perfect privacy even when a single base station and communication route fail simultaneously. Through rigorous mathematical proofs, the team demonstrates unconditional security, a significant advantage over encryption-based methods vulnerable to evolving computational capabilities. The achievement lies in constructing a system that guarantees information security without relying on complex mathematical problems, making it particularly suitable for resource-constrained devices, such as those used in military applications.
The researchers specifically demonstrate this security within a 3×3 configuration, representing a minimal yet effective setup for achieving both resilience and privacy. While the current work focuses on this specific configuration, the authors acknowledge that future research could explore the scalability of the scheme to larger and more complex network topologies. The team highlights the potential for extending this approach to enhance secure distributed storage systems, building on the foundation of XOR-based coding schemes already under investigation.