While Dynamic DNS addresses solve one problem about accessing self-hosted services outside your home network, they create their own issues. Having a public-facing IP address from your home network is never a good idea, even if you know enough to secure it against attack. Any open ports on your home IP address will get sniffed in short order.
It might make it easier for you to reach your NAS, but it does the same for any hackers. It’s the internet equivalent of saying, “Here’s my address and, by the way, I leave a window partly open at the back of the house otherwise I can’t sleep.” Sooner or later (usually sooner), someone will come to see if that’s true, and I don’t want to have to deal with the ensuing mess. Dynamic DNS might make sense if you’re a business, but even then there are better ways to access resources without exposing IP addresses to the wider internet.
Dynamic DNS has the same problems as static IPs
If your services and servers are open to the internet — someone you don’t want will find them
Having a static IP address, even one obfuscated behind dynamic DNS, is not something I’d recommend on your home network. If you were a business and needed a static IP, so customers could find you, I’d much rather suggest off-site managed hosting so that the hosting company is responsible for security, not you. Almost every home internet user is on a dynamic IP address, and that’s good. Why? Because the rotating IP addresses make it harder for anyone to track you and your devices, which keeps you safer overall.
What happens if you do have a static IP?
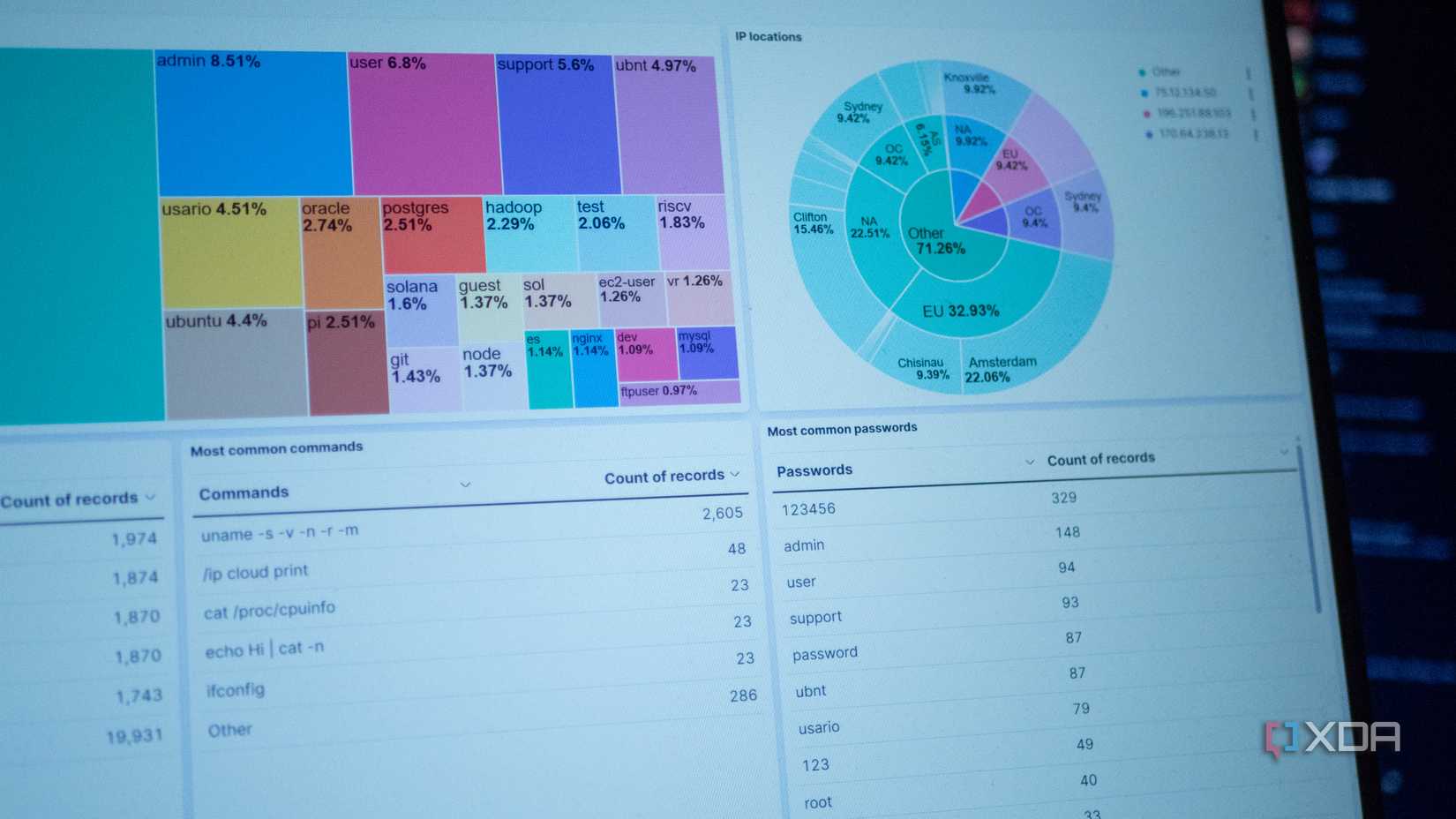
The image above is the analytics dashboard for Cowrie, an SSH honeypot I don’t recommend you set up at home. To the automated scanners hackers have set up, it looks like an SSH and Telnet instance with open ports to the internet. It is and it isn’t because it doesn’t connect to anything else in your computer, but simulates things so that the automated scans take interest.
And they will take interest. In just over a week, my colleague Adam showed nearly 30,000 unique interactions with the honeypot, with 447 unique IP addresses involved. These ranged from attempts to log into the service (with various password-stuffing methods), to scripts run against the instance to scrape more information, or even sending malware-filled files to the IP address in case it would accept them.
The 30K number is the number of interactions that could be logged. The real number, including port scans, will be several times this, all without the faked SSH connection even being used once. I don’t want to deal with that on my home network, and you shouldn’t either.
Why should anyone be able to see my IP address anyway?
When there are so many better options for remote access
You might not want to hear this, but most home users don’t want nor need a static IP, or to set up dynamic DNS to behave like one. The only reasons to have one nowadays are all business-focused ones, like point-to-point VPNs and even those can be set up without having to go through the added hassle of DDNS.
Instead of setting my self-hosted services behind DDNS, I have a cheap VPS that runs my remote access services. Currently that’s NetBird, but I’ve used a variety of tools in the past. This also runs a reverse proxy, so while there is only one public domain name, it can reach each of my services thanks to networking magic. It’s behind authentication, so scanners, scammers, and hackers get bounced, and only the VPS can see my home IP address.
But you don’t have to go that far. Tailscale will set up a peer-to-peer VPN mesh network in a matter of minutes, and keep your real IP address safely behind its own encrypted network. ZeroTier takes about the same amount of setup time, and dozens of WireGuard-based next-gen VPN solutions do the same thing: keep your home IP address out of the public eye while you’re self-hosting.
Or you could use Cloudflare in several ways
Cloudflare Tunnel gives you a secure, hands-off way to access self-hosted services like Nextcloud, in much the same way that WireGuard-based VPN solutions work. You don’t have to futz with firewall rules or worry about CG-NAT; it just works. It’s a quick-to-setup way to get access outside your home network, but there is another way with Cloudflare.
Now, I know I said I was done with DDNS, and that’s mostly true. But if you set Cloudflare as your DNS provider, they keep your home IP address obfuscated as if you were behind a VPN, as any attacker would only see the entrypoint into the Cloudflare network, not your NAS or home server. That makes Cloudflare DDNS better than other options that I’ve used. I still prefer to use WireGuard-based methods because then I ensure data is encrypted in transit, but it’s good to know you have other options.
DDNS is still useful, but I prefer to obfuscate my home IP address
The thing with almost every networking task is that there are a dozen (or more!) ways to accomplish the end result. That makes it more a question of priorities, like setup time, technical ability, whether you want to run services or have someone else handle that part, and so on. Your router might have its own DDNS service built in, like my Eero mesh does, but even with that, I still prefer the fully-encrypted methods using WireGuard. Security is always better when it’s a layered approach, and the more ways I secure my network and the data on it, the better.

