The official Xubuntu website was compromised over the weekend (18/19 October 2025) briefly serving up Windows malware to users trying to download the distro.
Users who visited the Xubuntu website over the weekend to download the official .torrent of the Xfce-toting Ubuntu flavour instead got a xubuntu-safe-download.zip.
When the rogue zip file was extracted it contained an .exe runtime and a ‘terms of service’ text file.
The Xubuntu team took down the affected download page as soon as they were informed. There is no indication that direct Xubuntu ISO downloads (or checksums) were modified, altered, replaced or otherwise interfered with.
The malicious download link appears to have been live for a day or two at most. Wayback Machine snapshots from 11 October point to the .torrent file, but the 18 October snapshot offers the malicious .zip instead.
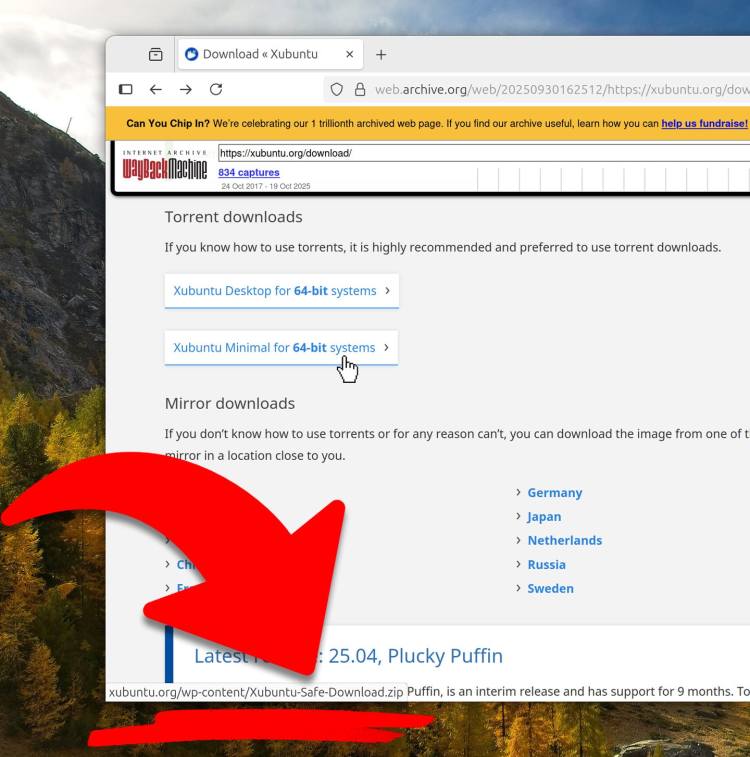 Only the torrent links served this
Only the torrent links served this
Was anyone affected?
I doubt anyone familiar with Linux would have been fooled by this — a Windows executable and the inclusion of a sloppily worded ToS are both redder-than-red flags — nor at risk, given the icky payload was designed for Windows.
But there is a chance that less tech-literate users running Windows could’ve been.
Indeed, exploiting that familiarity may have been the intention given the increasing interest in Linux distributions right now (thanks to Microsoft and the end of Windows 10 support – some folks don’t want to throw away their perfectly usable PC at the behest of Microsoft).
Per some sleuthing on Reddit, the exe package in the dodgy ZIP was found to contain malware made for Windows, which appears to be aimed at intercepting links for cryptocurrency accounts (because of course) that were copied to the clipboard.
How did this happen?
The torrent download links (and the entire download page) was disabled as soon as the Xubuntu team were made aware that something untoward had happened:
We’ve since taken down the download page and will be expediting our static site development to replace our aging WordPress instance.
Xubuntu Lead Sean Davies (on Mastodon)
Xubuntu team member Elizabeth Krumbach Joseph added more info in a follow up to the r/xubuntu sub-reddit: “We’re beholden to our hosting environment for upgrades and it looks like there was a bit of a slip-up here. It’s being worked on.”
As for what and how the torrent download link was made to point to malware, she adds that the team is is “in triage mode” and will share more “once they’ve completed remediation”.
The WordPress core is as secure as anything else. Broadly, the vast majority of WordPress security issues happen from vulnerabilities exploited in third-party plugins and themes that people add to their websites.
In the middle of this year, many commercial WordPress themes were found to have a flaw that attackers could use to upload ZIPs with backdoors in PHP files, and then add rogue admin users to modify site files. Not saying that happened here, but it underscores the point.
Was anything else affected?
To be clear: only the Xubuntu website torrent download link was affected. No other flavours, Ubuntu infrastructure, or other types of downloads were.
Ubuntu’s official flavours make use of Canonical-owned (and protected) infrastructure for image building and foundational needs, but hosting, design and security of each individual website is down to each flavour’s development team.
If you did not download Xubuntu from the official website using the torrent link during the short window this occurred, there’s no cause for concern. To download Xubuntu while the website download links are out of action you can use the Ubuntu CD Image server.
One to file under “keep calm and remember that people can be awful”.

